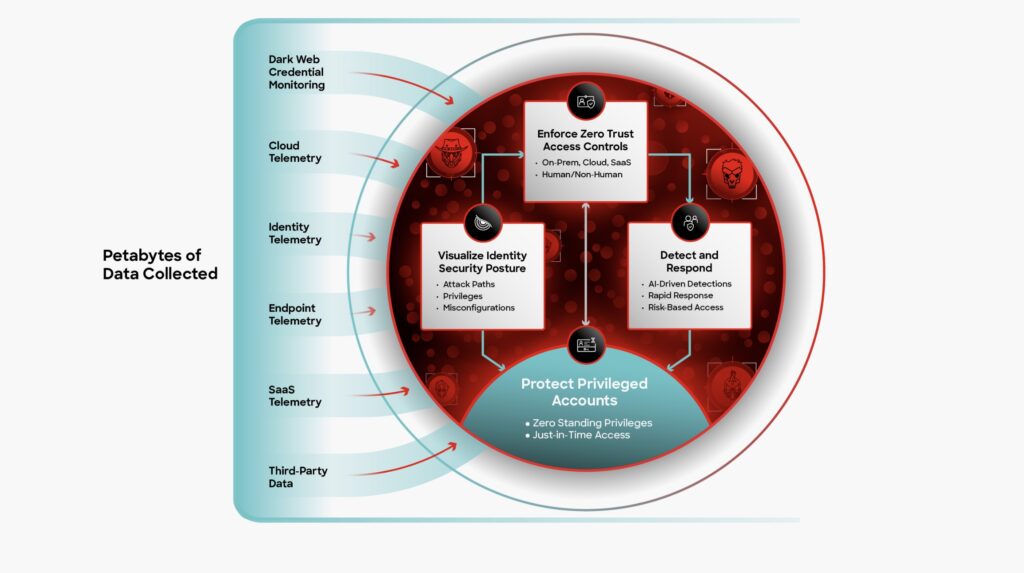
CrowdStrike recently introduced Falcon Privileged Access, a new component of its Falcon Identity Protection portfolio that adopts a just-in-time access model for privileged access management.
CrowdStrike also announced complementary capabilities, including integration between Falcon Identity Protection and Falcon Next-Gen SIEM, Charlotte AI Detection Triage for identity-based attacks, and new CrowdStrike Pulse Services for security maturity improvement.
These developments collectively expand CrowdStrike’s identity security capabilities while targeting operational challenges in identity-based threat detection.
Falcon Privileged Access
Unlike traditional Privileged Access Management (PAM) solutions that rely on standing privileges, Falcon Privileged Access implements dynamic permission controls integrated into CrowdStrike’s unified security platform.
The solution monitors user and device behavior using real-time signals from endpoints, threat intelligence, and AI analysis to dynamically grant, restrict, or revoke elevated permissions. This promises to address gaps in traditional PAM implementations while extending coverage across hybrid Active Directory and cloud environments without requiring infrastructure changes.
Core Architecture and Capabilities
Falcon Privileged Access operates on a just-in-time access model that evaluates security conditions before granting elevated permissions. This approach includes:
- Dynamic Access Controls: Permissions are granted at the moment of need based on security posture assessment
- Continuous Risk Assessment: User behavior and privilege status are analyzed against threat intelligence and security telemetry
- Hybrid Environment Support: Operation across on-premises Active Directory and cloud identity providers, including Microsoft Entra ID
- Zero Infrastructure Changes: Implementation without modifications to existing systems or separate access portals
- Unified Security Platform Integration: Incorporation into the CrowdStrike Falcon platform, utilizing its existing sensors and analytical capabilities
Falcon Privileged Access integrates with the broader CrowdStrike ecosystem:
- Operates within the Falcon platform architecture
- Utilizes existing endpoint sensors for behavioral monitoring
- Leverages the same threat intelligence feed that powers other Falcon components
- Provides visibility and policy enforcement
- Supports identity attack surface reduction across hybrid environments
Differentiating Features
The solution includes several capabilities that distinguish it from traditional PAM approaches:
- Real-time Signal Processing: Analyzes endpoint and device telemetry to assess contextual risk factors before granting privileges
- AI-Powered Behavioral Analysis: Uses AI trained on security events to detect anomalous behavior patterns
- Privilege Auto-Revocation: Withdraws elevated permissions when risk conditions change
- Forced Re-authentication: Can require users to re-validate identity when suspicious activities are detected
- Complementary PAM Integration: Works alongside existing PAM capabilities, including password vaulting and session recording
Other Announcements
In addition to its new Falcon Privileged Access, CrowdStrike also announced three complementary capabilities.
The updates collectively expand CrowdStrike’s identity security capabilities while targeting operational challenges in identity-based threat detection.
Falcon Identity Protection/Next-Gen SIEM Integration
The integration between Falcon Identity Protection and Falcon Next-Gen SIEM enables security teams to automate Active Directory response actions through Falcon Fusion SOAR without involving identity and access management teams.
This allows automatic enforcement of multifactor authentication and accelerate investigations through behavioral analytics.
Charlotte AI Detection Triage
Charlotte AI Detection Triage now autonomously analyzes identity-based attacks, trained on decisions from CrowdStrike Falcon Complete Next-Gen MDR to reduce alert fatigue and eliminate false positives.
CrowdStrike Pulse Services
The new CrowdStrike Pulse Services offers recurring micro-consulting engagements with dedicated security experts to help organizations improve security maturity through customizable engagement paths.
Impact to IT Practitioners
Falcon Privileged Access brings several operational advantages to IT and security teams:
- Administrative Workflow Changes: Reduces manual approval workflows while maintaining security controls.
- Decreased Standing Privileges: Minimizes the persistent attack surface presented by always-on administrative rights.
- User Experience Considerations: Enables access to legitimate workflows with fewer interruptions.
- Coverage Model: Protects both on-premises and cloud identity systems through a single control point.
- Integrated Approach: Potentially reduces the need for separate, siloed security tools.
Use Cases
Falcon Privileged Access addresses several use cases:
- Privileged Admin Access Control: Just-in-time elevation of privileges based on predetermined maintenance windows, ticket verification, and user/device risk assessment.
- Developer Environment Protection: Dynamic privilege assignment based on the development lifecycle stage, code check-in status, and threat intelligence indicators.
- Third-Party Vendor Access Management: Time-bound privilege elevation with monitoring of session behavior and revocation upon detecting anomalies.
- Cloud Resource Protection: Context-aware privilege elevation based on admin location, device security posture, and cloud activity patterns.
Analysis
CrowdStrike’s Falcon Privileged Access brings a different approach to privileged access management that’s aligned with current threat patterns. The new solution closes gaps in identity security while reducing operational friction by moving from traditional standing privilege models to dynamic, just-in-time access based on risk assessment.
The integration within the Falcon platform provides several advantages, notably the ability to incorporate endpoint telemetry, threat intelligence, and AI-powered analysis into access decisions. This contextual awareness enables more informed risk assessment than many standalone PAM tools provide.
As identity-based attacks continue to increase, CrowdStrike’s approach to privileged access connects security controls with contemporary attack methodologies. The integration with Charlotte AI for detection triage shows CrowdStrike’s strong focus on addressing operational challenges of identity threat detection.
This is a strong addition to CrowdStrike’s portfolio.
Competitive Outlook & Advice to IT Buyers
Competitively, this brings CrowdStrike into an environment where it now competes with both competitive PAM vendors and identify providers with an approach that spans security domains.
While established PAM vendors offer deeper specialized capabilities, they typically lack CrowdStrike’s endpoint visibility and threat intelligence integration.
| Capability | Traditional PAM Vendors | Identity Providers | CrowdStrike Falcon Privileged Access |
| Access Model | Standing privileges with check-out workflows | Role-based access controls | Dynamic just-in-time privileges |
| Deployment | Separate infrastructure | Identity system integration | Security platform integration |
| Risk Assessment | Policy-based | Limited contextual awareness | Endpoint and identity telemetry |
| Response Actions | Mostly manual | Limited to identity systems | Automated across endpoint and identity |
| Intelligence Sources | Limited threat integration | User attributes | Threat intelligence integration |
| Hybrid Coverage | Often requires multiple products | Provider-specific | Coverage across on-prem and cloud |
…
These sections are only available to NAND Research clients AND IT ADVISORY MEMBERS. Please reach out to [email protected] to learn more.