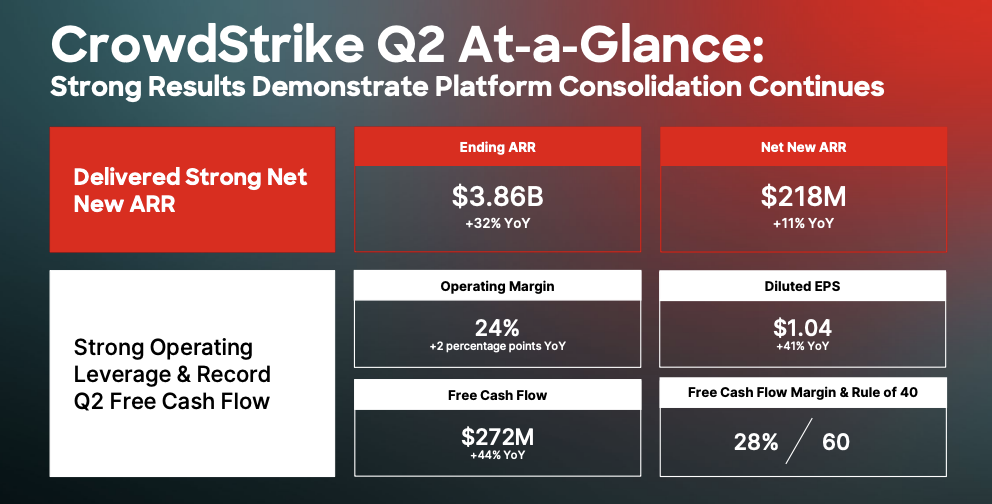
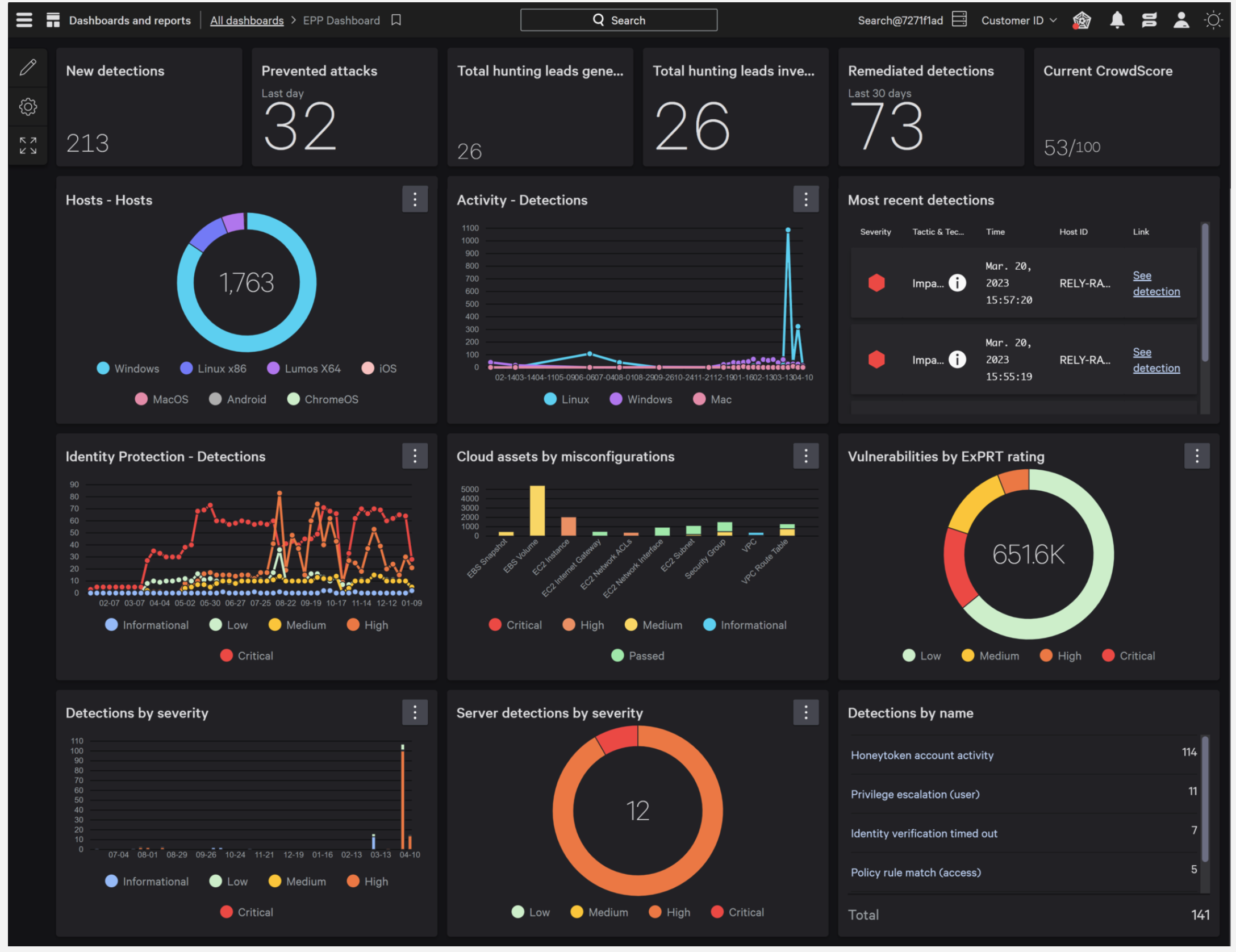
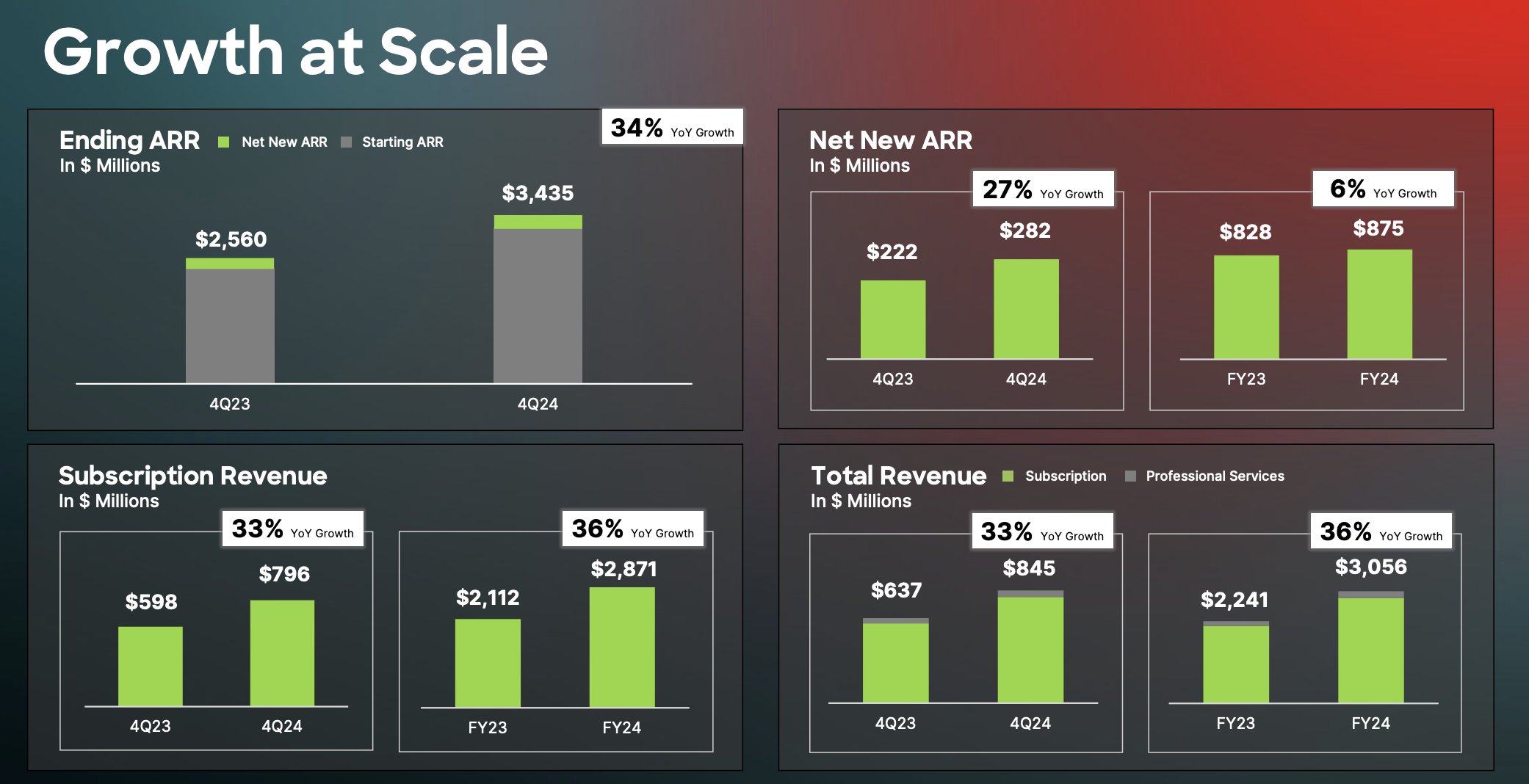
CrowdStrike expanded its threat-hunting capabilities, introducing its new Falcon Adversary OverWatch Next-Gen SIEM, extending visibility beyond endpoints to third-party data sources.
The new solution uses managed threat hunting to uncover threats in their early stages using available third-party SIEM data from network edge devices, identity and access management tools, SaaS applications, and email security tools.
Key innovations in the new solution include expert-led threat hunting across all attack surfaces, advanced user behavior analytics, case management, and identity security automation.
Technical Overview & Key Features
Falcon Adversary OverWatch Next-Gen SIEM brings real-time managed threat hunting to available third-party SIEM data, complementing CrowdStrike’s existing first-party threat-hunting capabilities across endpoint, cloud, and identity.
The new solution uses AI, deep adversary expertise, and threat intelligence to uncover threats while unifying native and third-party data, real-time intelligence, and AI-driven automation to deliver full visibility, high-fidelity alerts, and accelerated response.
It also integrates Falcon Identity Protection with Falcon Next-Gen SIEM to combine identity insights with threat intelligence, endpoint activity, and behavioral analytics. Falcon Fusion SOAR enables automated enforcement of identity policies, while unified visibility helps analysts prioritize identity-based threats.
Key Capabilities
- Threat intelligence enrichment: Falcon Adversary OverWatch enriches SIEM events with threat intelligence and expert investigation results, using AI to transform large volumes of telemetry into high-confidence alerts
- Correlation engine: The system correlates signals, analyzes behaviors, filters out false positives, and surfaces threats across environments
- Collective defense model: When a threat is uncovered in one environment, the system checks across all environments to determine whether others are at risk, enhancing protection across all customer environments
- Data processing capabilities: Analyzes up to 4.7 trillion events daily with 24/7 expert-driven threat-hunting
UEBA Capabilities
New UEBA capabilities deliver behavior-based threat detection powered by automation, AI, and contextual awareness to address gaps in traditional tools.
Falcon Next-Gen SIEM correlates detections across users, hosts, and activities to uncover insider threats and disguised adversary behavior.
The UEBA component includes:
- AI-powered risk scoring: Prioritizes high-fidelity detections by assigning risk scores that reflect incident urgency
- Automated entity resolution: Accelerates investigations by eliminating manual data correlation
- Attack timeline visualization: Provides visibility into attack progression, including involved parties, actions taken, and timing
- Customizable risk scoring: Allows organizations to adjust scoring parameters based on their environment
Impact to IT Teams
CrowdStrike’s new solution brings several new operational benefits to IT organizations:
- Reduced tool sprawl through consolidated security operations in a unified platform
- Lower MTTD by extending expert-led threat hunting across environments
- Decreased alert fatigue through AI-powered risk scoring and false positive reduction
- Streamlined investigations via automated entity resolution and timeline visualization
- Enhanced operational metrics through case management dashboards
The new offering is ideal for multiple use cases:
- Extended Threat Hunting Across Network Edge: Detect threats targeting key entry points such as firewalls, routers, VPNs, and email gateways. Security teams gain visibility into adversary activity at network boundaries before it progresses to endpoints.
- Insider Threat Detection: UEBA capabilities correlate detections across users, hosts, and activities to uncover insider threats and other activities adversaries disguise as normal behavior.
- Unified SOC Operations: Integrated case management allows analysts to build cases from detections or scratch, using pre-defined or customizable templates to guide triage and resolution.
- Identity-Based Attack Detection and Response: Integrating Falcon Identity Protection with Next-Gen SIEM enables security teams to detect and prioritize identity-based threats in real-time, with automated enforcement through Falcon Fusion SOAR.
Analysis
CrowdStrike’s Falcon Adversary OverWatch Next-Gen SIEM expands managed threat-hunting capabilities beyond the company’s traditional focus areas. In bringing expert-led hunting to third-party data, CrowdStrike addresses critical gaps in visibility that adversaries exploit to bypass security controls.
The integration of advanced UEBA, case management, and identity protection capabilities further enhances the platform’s overall value proposition.
The extension of OverWatch to third-party data is a significant evolution of CrowdStrike from an endpoint security vendor to a comprehensive security platform provider. Its direction aligns with broader market trends toward consolidated security operations and intensifies competition with established SIEM players.
CrowdStrike’s Adversarial OverWatch delivers demonstrable threat detection improvements while simplifying complex security operations, something CrowdStrike has always done well. This is a strong new offering that provides CrowdStrike with compelling differentiation.
Competitive Outlook & Advice to IT Buyers
CrowdStrike is positioning the new offering as the first to bring managed threat-hunting capabilities to third-party data, differentiating itself from competitors who either:
- Focus exclusively on their own telemetry
- Provide SIEM capabilities without integrated threat-hunting
- Offer managed detection but lack the scale and AI capabilities of the Falcon platform
Extending OverWatch to third-party data is an advancement to CrowdStrike’s platform approach, moving beyond endpoint-focused security to comprehensive security operations across all attack surfaces.
Here’s how we see its competitive fit in the market…
These sections are only available to NAND Research clients and IT Advisory members. Please reach out to info@nand-research.com to learn more.