OpenText recently announced its new Core Threat Detection and Response, an AI-driven cybersecurity solution that will become generally available with its Cloud Editions 25.2.
The new platform integrates with Microsoft security tools, including Microsoft Defender for Endpoint, Microsoft Entra ID, and Microsoft Security Copilot, to enhance threat detection and response capabilities. The solution operates as an Open XDR (Extended Detection and Response) platform, enabling enterprises to integrate telemetry from multiple security tools and applications.
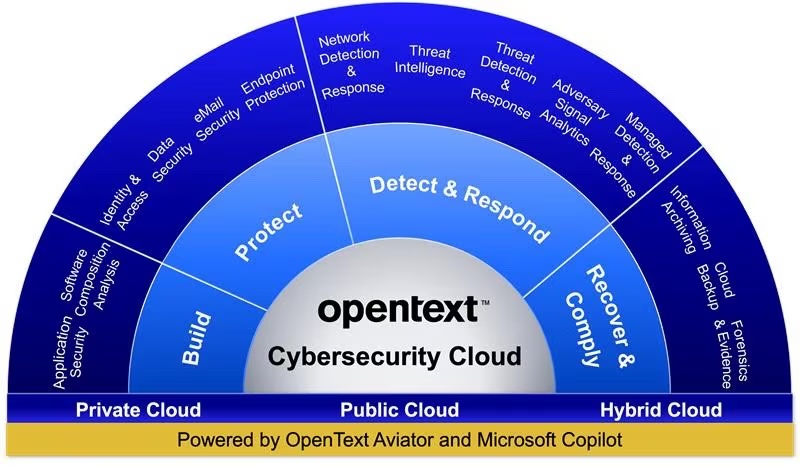
OpenText’s Core Threat Detection & Response
Core Threat Detection and Response incorporates machine learning models to analyze security events and detect threats beyond rule-based mechanisms. The platform includes several key components:
- Behavioral Analytics: Utilizes machine learning to identify anomalies in user and entity behavior, detecting insider threats, credential misuse, and unauthorized access attempts.
- Adaptive Threat Detection: Continuously refines its detection models based on evolving enterprise activity patterns, reducing false positives and improving response accuracy.
- Automated Correlation: Analyzes security logs, network traffic, and endpoint data in real-time to identify multi-stage attacks.
- Threat Integration Studio: Allows enterprises to ingest and analyze telemetry from third-party security solutions, reducing security silos.
- Contextual Alerting: Uses AI-driven insights to generate alerts with detailed explanations, reducing the burden on security operations center (SOC) teams.
- Multi-Cloud Integration: Supports deployment on Microsoft Azure, with planned expansion to additional cloud platforms.
OpenText’s Core Threat Detection and Response is a composable solution that integrates with existing security ecosystems. OpenText emphasizes interoperability, allowing enterprises to augment their current security infrastructure without replacing existing tools.
The platform supports:
- Microsoft Security Stack Integration: Deep integration with Microsoft Defender, Entra ID, and Security Copilot enhances threat detection within enterprise Microsoft environments.
- Cross-Solution Compatibility: The Open XDR architecture enables integration with other security platforms, ensuring compatibility with identity management, endpoint protection, and data loss prevention tools.
- Simplified Deployment: Pre-built integration kits reduce setup time, enabling enterprises to extract value from the platform with minimal configuration.
Analysis
OpenText manages much of the world’s enterprise data. This makes it an ideal platform on which to host cybersecurity and data protection capabilities. The company understand that, and its new Core Threat Detection and Response capabilities are a nice addition to OpenText’s cybersecurity capabilities.
The platform competes well against established XDR solutions, including Palo Alto Networks Cortex XDR, Microsoft Sentinel, and CrowdStrike Falcon XDR. Several factors influence its strong competitive position:
- Alignment with Microsoft Security Ecosystem: The platform’s deep integration with Microsoft security tools enhances its appeal for organizations invested in Microsoft environments. It may, however, face limitations in non-Microsoft-centric enterprises.
- AI-Driven Threat Detection: Core Threat Detection and Response differentiates itself through its AI-based behavioral analysis, potentially reducing false positives compared to rule-based security solutions.
- Market Entry Timing: OpenText enters the AI-powered threat detection space at a time when security teams face increasing challenges from insider threats and alert fatigue. The emphasis on contextual threat insights may address key pain points for SOC teams.
- Expansion Potential: OpenText plans to extend its integrations beyond Microsoft security tools, broadening adoption among enterprises using heterogeneous security stacks.
Its AI-driven insider threat detection and anomaly correlation approach addresses SOC alert fatigue, a growing industry challenge. If OpenText successfully expands support beyond Microsoft environments, it will be well-positioned as a strong alternative to traditional rule-based XDR solutions.
Competitive Outlook & Advice to IT Buyers
These sections are only available to NAND Research clients. Please reach out to [email protected] to learn more.