Cloud security provider Lacework recently announced the extension of its platform to include code security, enhancing its coverage of the full application lifecycle. The new features provide Lacework customers with comprehensive visibility throughout the application development process, helping to identify and address security issues before deployment.
New: Software Composition Analysis
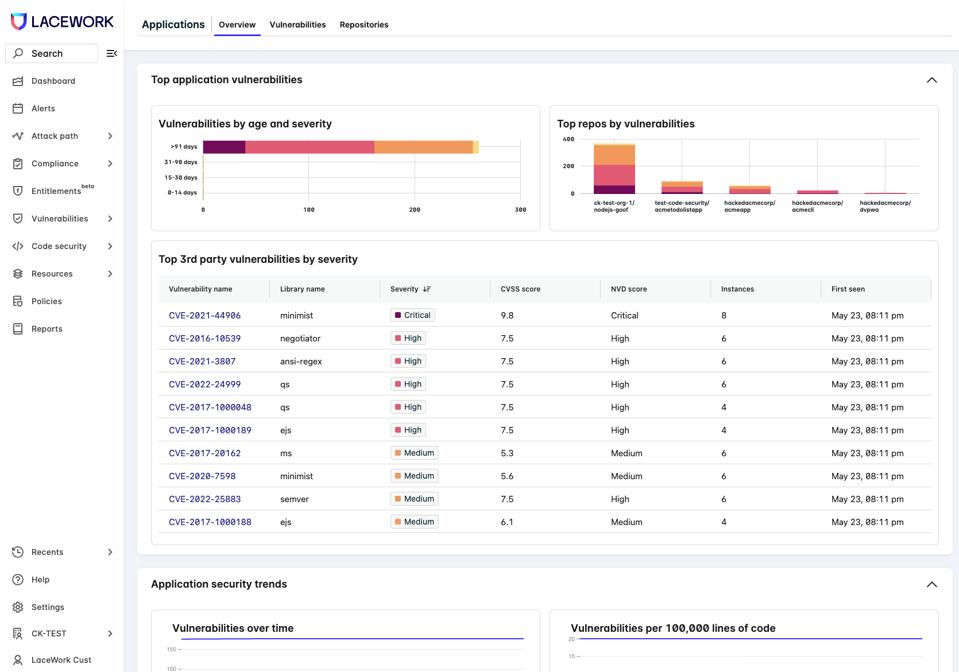
Lacework’s new SCA tools focus on providing continuous visibility into third-party software libraries within customers’ repositories and protecting the software supply chain. The solution offers several unique and differentiating features that enhance its effectiveness in managing third-party code vulnerabilities:
- Continuous Visibility and Tracking: Lacework SCA provides continuous visibility into third-party software libraries used in customer repositories. This includes direct and indirect dependencies, offering a comprehensive view of the software supply chain.
- Detailed Vulnerability Insights: Beyond basic SCA functionalities, Lacework delves into specific details like where vulnerable functions are used in the code, the frequency of their use, and identifying responsible parties for introducing and fixing vulnerabilities.
- Real-time Software Bill of Materials (SBOMs): Lacework maintains an always up-to-date SBOM for every application. This feature is essential for understanding the components that make up software applications and managing associated security risks.
- Extended to Cloud-Native Workloads: Lacework extends its SCA capabilities to include visibility of vulnerable packages throughout their lifecycle, from their usage in source code to their activity in cloud-native workloads. This holistic view is crucial for comprehensive security management.
- Active Vulnerability Detection (AVD): The integration of AVD with the Lacework runtime agent, known as the Code Aware Agent (CAA), allows for identifying runtime package activity across various cloud workloads. This feature enhances the detection and management of vulnerabilities in real time.
- Prioritization Based on Actual Use: Lacework’s SCA allows organizations to prioritize updates or removal of packages based on their actual activity. This approach helps efficiently allocate resources to address the most critical vulnerabilities first.
- Understanding Open-Source License Risks: Along with security vulnerabilities, Lacework SCA also provides insights into open-source license risks, a crucial aspect of compliance and risk management in software development.
- Combining Static and Runtime Analysis: The unique approach of combining static program analysis with runtime insights offers a more dynamic and effective method of detecting and managing vulnerabilities in software applications.
These features make Lacework’s SCA a powerful tool for enterprises, providing a deeper and more actionable understanding of third-party code vulnerabilities, thereby enhancing their software applications’ overall security posture and compliance.
The new SCA capabilities will help organizations maintain an up-to-date software bill of materials (SBOMs) for every application and provide continual visibility into their software supply chain, including understanding open-source license risks.
New: Static Application Security Testing
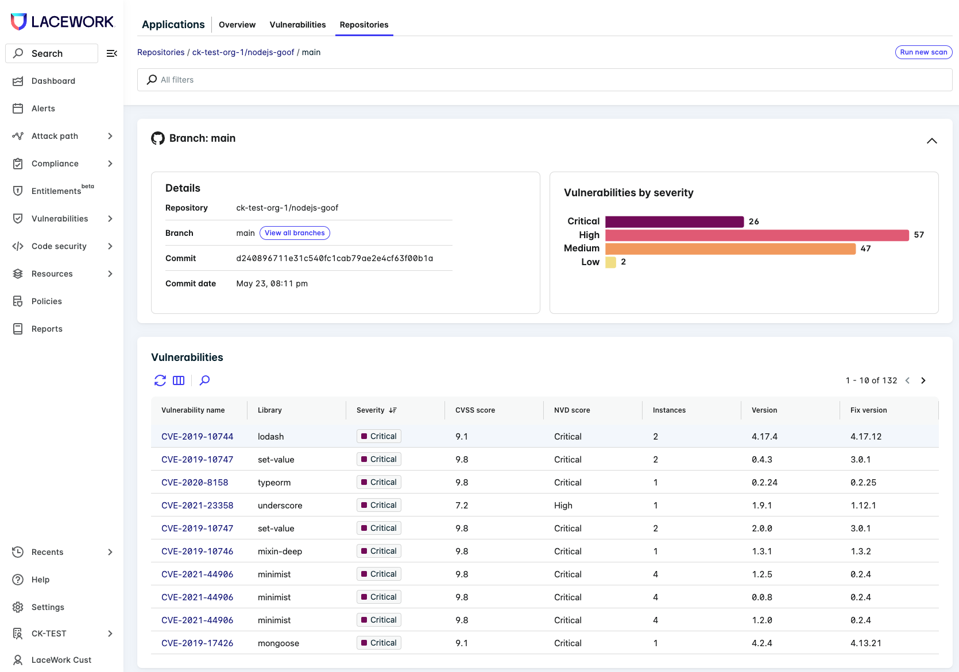
Lacework’s SAST capabilities provide visibility into complex vulnerabilities in internet-facing applications and include a sophisticated analysis of call chains and control paths to identify potential security risks with low false positives and negatives.
The new SAST tool has several unique and differentiating features that set it apart from traditional SAST solutions:
- Sophisticated Analysis Techniques: Lacework SAST utilizes advanced methods to analyze an application’s call chains and control paths. This deep analysis helps in understanding the context of the code, leading to more accurate identification of potential security vulnerabilities.
- Low Rate of False Positives and Negatives: A common issue with traditional SAST tools is the high rate of false positives and false negatives. Lacework’s SAST is designed to minimize both, providing more precise and reliable results.
- Integration of Compensating Controls Recognition: The tool can recognize when developers have implemented compensating controls in the code to mitigate risks. This feature ensures that the security analysis is more aligned with the actual security posture of the application.
- Customization and Configurability: Lacework allows security engineers to customize and add rules tailored to the specific needs of their unique codebase. This level of configurability ensures that the tool can adapt to a wide range of applications and security requirements.
- Speed and Scalability: Lacework SAST is designed to be fast and scalable, capable of assessing millions of lines of code in minutes. This feature is particularly beneficial for large-scale enterprise applications and rapid development environments.
- Comprehensive Visibility into Vulnerabilities: Lacework SAST provides in-depth insights into potential vulnerabilities, especially in internet-facing applications. It tracks the path of untrusted data to identify zero-day vulnerabilities that could lead to serious exploits like SQL injection.
- Enhanced Security Posture: By integrating sophisticated analysis and precise results, Lacework’s SAST tool improves the overall security posture of applications, enabling security teams to address vulnerabilities more effectively.
These features work together to make Lacework’s SAST a robust and efficient tool for modern application security, helping organizations to secure their first-party code with higher accuracy and less operational overhead.
Analysis
The new code protection tools extend Lacework’s platform to cover the complete application lifecycle, enhancing its capabilities in code and cloud security. This enables enterprises to innovate and deliver secure cloud-native applications more effectively.
Lacework isn’t alone in delivering tools to protect the application lifecycle—it’s a crowded market. Vendors such as Lacework, Snyk, Rapid7, and Palo Alto Networks, among others, all provide pieces of the puzzle, but Lacework is one of the very few that delivers full application lifecycle protection.
The newly introduced features provide Lacework customers with comprehensive visibility throughout the application development process, helping to identify and address security issues before deployment.
By integrating code security into its platform, Lacework unifies code and cloud security, allowing enterprises to develop and deliver secure cloud-native applications more efficiently. The ability to provide integrated cloud and application lifecycle protection is a significant differentiator for Lacework. We like the approach.