Palo Alto Networks has unveiled the latest iteration of its leading Prisma Cloud offering, which it calls “Darwin.” The new Prisma Cloud release introduces tools and features that secure the entire application lifecycle, from the code’s inception to its deployment and runtime in the cloud.
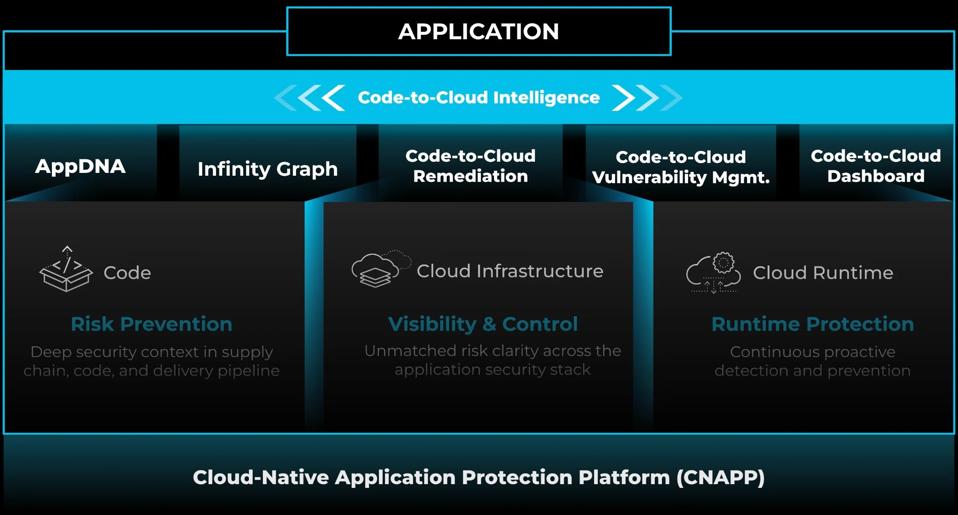
New: Code-to-Cloud Intelligence
Palo Alto Networks takes a game-changing approach to minimizing threats across the full application lifecycle. Its Code-to-Cloud approach dives deep into patterns, behaviors, and anomalies across code, cloud infrastructure, and runtime. Not only does this help identify security issues, but it traces them back to their source in the code, allowing for effective remediation right at the point of origin.
Dashboard
The Code-to-Cloud Dashboard within Prisma Cloud provides visibility and control across the entire application lifecycle, from its inception to its deployment and operation in the cloud.
The dashboard provides comprehensive visibility with its centralized view spanning the entire software development lifecycle. This ensures that stakeholders can monitor and assess the status and security of applications at every stage.
More than just a monitoring tool, the Code-to-Cloud Dashboard provides analytics, delivering insights into each stage of the software development process, which facilitates rapid data-driven decisions.
The dashboard is also designed to make reporting on application and security metrics easier to deliver to leadership and boards. It streamlines the process of communicating key metrics and insights to stakeholders.
The Code-to-Cloud Dashboard is a comprehensive tool for organizations to monitor, analyze, and report on their applications’ status and security from development to deployment in the cloud. With the aggregated data and insights, IT teams can make more informed decisions for application development, deployment, or security mitigation measures.
Vulnerability Management
Prisma Cloud’s new Code-to-Cloud Vulnerability Management enables a comprehensive approach to identifying, managing, and mitigating vulnerabilities throughout the entire application lifecycle.
While vulnerabilities are a reality in the digital landscape, the key is in how quickly and efficiently they can be addressed. Traditional methods might take months to patch a vulnerability due to a lack of context and reliance on older workflows.
Code-to-Cloud Vulnerability Management addresses this, offering a broad view of vulnerabilities that allows teams to trace them back to their source. This can be the base image, code repository, or other origin. These insights allow vulnerabilities to be addressed at the source, ensuring that subsequent deployments or “pipeline pushes” are secure by design.
A key advantage of this approach is that it allows for vulnerabilities to be fixed at their origin. Instead of applying patches or fixes at the end of the development cycle or after deployment, vulnerabilities can be addressed where they begin – in the code itself or the initial stages of the development and deployment pipeline.
Remediation
Code-to-Cloud Remediation allows IT teams to address and rectify security issues and vulnerabilities across the entire application lifecycle. While traditional remediation often involves a ticket-based approach, which can be inefficient and time-consuming, Code-to-Cloud Remediation allows risks identified in the cloud to be immediately rectified, streamlining the response to security threats.
Remediation is about more than just addressing the immediate issue. Prisma Cloud traces risks back to their origin in the codebase. By identifying the root cause of a vulnerability, it ensures a more thorough and effective solution.
Once a risk is traced back to its source in the code, a pull request can be initiated for developers. This allows developers to immediately address the issue, preventing the same vulnerability from recurring in future iterations or deployments.
By tackling vulnerabilities at their source and integrating the fixes into the codebase, Palo Alto’s Code-to-Cloud remediation approach ensures that the same issues don’t arise in future deployments. This proactive stance towards security helps maintain a robust and secure cloud environment.
New: AppDNA
AppDNA modernizes the visibility of cloud applications by providing a structured, application-centric view. The tool showcases the components or “DNA” of the cloud applications, which includes cloud services, infrastructure assets, compute workloads, API endpoints, data, and the actual code that makes up these applications.
AppDNA offers users a comprehensive and intuitive view of their cloud applications and all the components that constitute them, all in one place. This enhanced visibility is complemented by additional cloud and business context, providing users with a more holistic understanding of their cloud apps.
New: Infinity Graph
Prisma Cloud’s new Infinity Graph is designed to help users better understand and contextualize risks associated with their applications and infrastructure. Here’s a breakdown of what the Infinity Graph does:
- Deep Context on Risks: It provides deep insights into potential security risks by correlating the security stack across various elements like misconfigurations, vulnerabilities, exposures, identities, secrets, sensitive data, and more.
- Potential Attack Paths: Beyond merely identifying risks, the Infinity Graph visualizes possible attack paths that could lead to a security breach. This aids organizations in preemptively addressing vulnerabilities before they are exploited.
- Real-time Threat Visualization: The graph overlays active attack attempts, showing users what threats are active and if any protections are in place.
- Interactivity: It is highly interactive, allowing users to ask questions, explore issues, and investigate from code to cloud. This feature is handy for security professionals to efficiently perform forensics and set up guardrails from the supply chain to the application runtime.
The Infinity Graph offers a comprehensive visual representation of the security landscape, enabling users to quickly understand, investigate, and respond to potential and active threats.
Analysis
Cloud-native development and cloud applications have revolutionized the modern enterprise. While this has brought incalculable benefits to IT organizations, it has also introduced new risks. These applications are often vulnerable due to the intricate blend of software packages they’re built from, with threats ranging from code misconfigurations to unpatched vulnerabilities.
This landscape is further complicated by a software supply chain that extends beyond a single organization, instead involving multiple vendors, partners, and open-source ecosystems. The new Prisma Cloud release addresses these challenges, delivering a significant advancement in CNAPP that ensures security across the application lifecycle from code to cloud.
The new Darwin release of Prisma Cloud represents a significant advancement in cloud security, equipping organizations with the tools and intelligence they need to navigate the complexities of modern cloud-native applications. It emphasizes proactive risk management, deep insights, and a holistic approach to security from code to cloud.
Palo Alto Network’s commitment to innovation, combined with its impressive cadence of release, cements Prisma Cloud’s position as the premier CNAPP solution in the market. This continues with the latest release, making Palo Alto Networks uniquely equipped to deliver Code-to-Cloud Intelligence–precisely what’s needed in today’s cloud-driven world.